Blog

OneSite Health, Security & Compliance
How Breaches Like Log4J Are Making IT Teams Rethink Their Lines of Defense
Apr 14, 2022
Last December, a flaw in widely used internet software known as Log4J left companies and government officials scrambling to respond to a massive cyber...

Security & Compliance
Endpoint Security Should Be Top Priority for IT, New Research Shows
Apr 13, 2022
New research shows that cybersecurity threats are on the rise, but IT teams' confidence in their endpoint security solutions, processes, and staff is ...
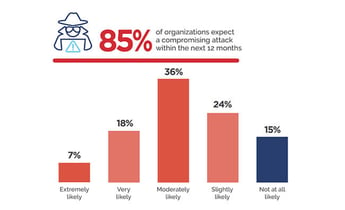
Security & Compliance, News & Press
85% of Organizations Expect a Compromising Attack in the Next Year, Adaptiva Research Reveals
Apr 13, 2022
New research from Adaptiva and Cybersecurity Insiders reveals a stark cybersecurity reality – security threats are increasing rapidly while confidence...

Security & Compliance
Can zero trust really protect government from cyberattacks?
Jun 2, 2021
It’s clear from the recent spate of cyberattacks on government networks, be it the SolarWinds incident or the Russian intelligence breach of the Treas...

Security & Compliance
5 Things To Think About When Shifting to Zero Trust
May 18, 2021
The pandemic has sent cyberattacks into overdrive. Hundreds of millions of attacks were initiated each day of 2020 and malware increased by 358% last ...

OneSite Health, Security & Compliance, Operations
Automation Solutions Key to Ensuring Security and Protection in Remote Environments
Mar 5, 2021
IT teams cater to the sometimes daunting, often mundane task of persistently securing and maintaining thousands of endpoints. Running health checks an...

Security & Compliance, News & Press
IT Professionals Reveal Scanning Endpoints for Vulnerabilities as Their Top Cybersecurity Challenge
Oct 31, 2019
Adaptiva Shares Results of Fourth Annual Enterprise Endpoint Security Survey Just 17% of companies have enough staff to handle security appropriately ...

Security & Compliance, MVP
OneDrive Gets a Personal Vault, and VPNs Offer Less Security than Ever
Jul 8, 2019
This week’s security snacks:

Security & Compliance, MVP
Smart TV Insecurities, Home Devices Even Less Secure Than We Thought, and Half of the World’s Email Servers at Risk
Jun 19, 2019
In this week’s security snacks:

Security & Compliance, MVP
RDP Gates Remain Open, Spying as a Service, and G-Suite Cleartext Passwords
May 30, 2019
This week’s security snacks:

Security & Compliance, MVP
Data-Stealing Drones, Insta-GramScamming, and Google Yanks Huawei’s Android License
May 22, 2019
This week’s security snacks:

Security & Compliance, MVP
Matrix-Themed Ransomware and Malware Vulnerability-Scanning the Internet
May 13, 2019
MegaCortex Sends Your Data Down the Rabbit Hole Bite The latest in the long line of ransomware variants, MegaCortex is a nod to a particular Keanu Ree...
FEATURED
Streamline Patching Workflows and Expedite Patch Compliance with Automated Approval Chains
Rev Up Your Endpoint Security with Adaptiva at These Upcoming Events
Adaptable Automation: Balancing Speed With Enterprise Complexities
Accelerate Critical Updates and Control Patching Automation with Deployment Bots
Practitioner Series
In these blog posts, we share what we know about managing endpoints. Stop by to hear from our own in-house subject matter experts. We are excited to discuss best practices, technical how-tos, and other topics we think you'll find valuable. Our solution architects, product experts, and own IT practitioners have seen and done it all. We are adding new content regularly and are happy to have you here.






































