Last December, a flaw in widely used internet software known as Log4J left companies and government officials scrambling to respond to a massive cybersecurity threat to global computer networks.
Log4J--widely used in a variety of consumer and enterprise services, websites, and applications--was a vulnerability that left a huge hole for bad actors to exploit. But, according to a recent study published by Adaptiva and Cybersecurity Insiders, 85% of organizations are simply expecting a compromising attack this year.
Key article takeaways
- 85% of organizations expect a compromising endpoint attack in the next 12 months (despite only 20% of them being compromised last year)
- Almost half of organizations' installed legacy security products (AV, NGAV, HIPS, EPP, etc.) are failing to stop an increasing number of evolving threats
- Even organizations who believe they have solid endpoint management tools and processes in place are still concerned that threats are slipping through the defenses.
- Starting, stopping, pausing, and reprioritizing deployments of software, configurations, remediations, and patches should be easier (and can be).
The growing threat landscape
The dust hadn’t settled with Log4J when in early January Google issued a warning via it’s Chromium bug tracker to its nearly 3-billion users of the Chrome internet browser that a “forthcoming update could break a number of websites around the world.” Tuesday, February 1st, those warnings came true when Google published a blog confirming 27 exploits had been discovered. Google warned that eight are classified as posing a ‘High’ threat level.
It’s not just Adobe, Google, Microsoft, Amazon and other major tech giants that are feeling the crunch from a growing list of cybersecurity threats, it’s every IT person in every company around the world. A recent study released by Adaptiva, in partnership with Cybersecurity Insiders, reveals 85% of organizations expect a compromising security attack within the next 12-months.
 "85% of organizations expect a compromising security attack within the next 12 months."
"85% of organizations expect a compromising security attack within the next 12 months."
- The 2022 Endpoint Security Report from Adaptiva and Cybersecurity Insiders
The threats keep coming and the resources continue to dwindle or are insufficient for the problems at hand.
- 66% of organizations have experienced increased threats to their endpoints in the last year
- 44% face a cybersecurity skills shortage
- 38% lack round-the-clock security coverage
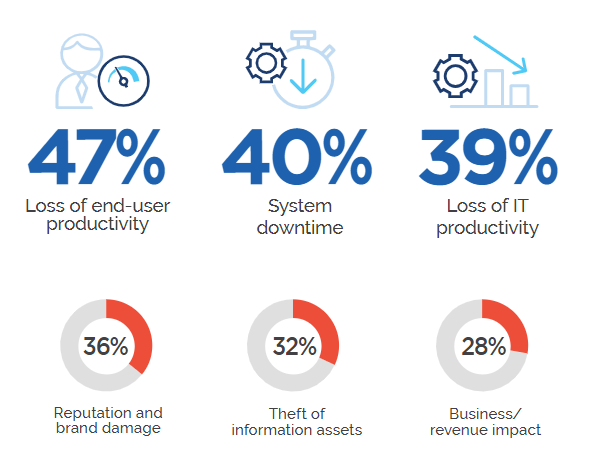
But where the rubber hits the road is the compounding impact these breaches have on organizations--impacts that can be felt from C-Suite to IT Managers down to the end-user (a major problem for companies prioritizing digital transformation efforts and remote work). Surveyees from The 2022 Endpoint Security Report chose the greatest impacts these threats have on their business and the results are staggering.
So, how do IT teams adapt in the face of growing endpoint threats?
- Turn each member of their IT staff into endpoint remediation experts by automating manual endpoint configuration checks and remediations ensuring compliance and security
- Get real-time visibility and control no matter a devices location to start, stop, pause and reprioritize deployment of software, configurations, remediations, patches, and more.
- Deliver critical content to any device, at any time of day, without impacting network or device performance.
But, according to the data from the report, seems to be easier said than done. Especially, if you consider that many installed legacy security products (AV, NGAV, HIPS, EPP, etc.) are failing to stop an increasing number of evolving threats. And even organizations who believe they have solid tools and processes in place are still concerned that threats are slipping through the defenses.
A multitude of endpoint management and security companies jumped at the opportunity to effectively guide customers through the Log4J crisis. Our customers--many with hundreds of thousands of endpoints on their network needed an automatic, lightning fast solution to remedy the impending damage this vulnerability was going to cause.
Custom health checks are faster (and more effective) than Powershell scripts
Let's take a closer look at how Endpoint Health, which leverages The Adaptiva Edge Platform, was able to remediate any issues of infected Log4J files.
Within a matter of hours of the announcement of the Log4J threat, Adaptiva jumped into action and created a brand-new custom health check using their Endpoint Health workflow authoring tool. Once the workflow had been created customers could leverage the new Log4J health check to quickly and easily, using the Adaptiva Edge Platform, check each one of their global endpoints and identify any endpoint that had the affected version.
You can read Adaptiva's full Log4J FAQ here.
As more information surfaced, Adaptiva was able to, in real-time, react and revise the workflow to stay one step ahead of bad actors who were trying to exploit the vulnerability.
Without Adaptiva, IT teams would be forced to research and create Powershell scripts which depending on the expertise level could take hours or days to complete. Without the power of the Adaptiva Edge Platform, IT staff would be forced to work late into the night once their end users had gone home to push the scripts and attempt to get ahead of the growing threat.
The Adaptiva Edge Platform allows organizations to push health checks, remediations, and content patches in real time without ever throttling the network or adversely affecting the end user.
Due to the sheer size and scope of the Log4J vulnerability Adaptiva, in partner with many of their customers identified, built, and rolled out the custom Log4J remediation in a week. On average each customer affected would find anywhere from 5 to 8 issues of infected Log4J files on endpoints throughout their network. The remediation was able to help them automatically delete those affected files.
Don't wait for the next cybersecurity threat
Join Adaptiva's Solutions Architect, Alphaeus Mote and Product Marketing Director, Matt Mayhew in an upcoming webinar to learn more.
Effective, comprehensive endpoint management is crucial to security and success in the modern workplace. Without a well-functioning endpoint management system, a company is vulnerable to ever-increasing cyberattacks and losing control over its data, assets, and network. Legacy endpoint management systems claim to close the door on malicious attackers. But, what good is closing the door when you’ve left the windows open? Why are so many companies stuck on legacy systems that pose innumerable risks and frustrations? And, not to mention, these legacy systems require equipment, human hours, maintenance costs, and, in turn, hundreds of thousands, if not millions, of dollars spent on systems that cannot effectively or efficiently scale. If Fortune 500 enterprises are spending that kind of money on systems that don’t even do a good job of keeping their endpoints continually in compliance, then what is it all for?
The Adaptiva Edge platform, which includes Endpoint Health and OneSite Anywhere, can be a powerful tool for organizations to detect and remediate endpoints affected by the latest vulnerabilities, such as Log4J. Adaptiva has historically built new custom health checks and custom auto-remediations whenever bad actors or new vulnerabilities arise. This helps organizations easily identify endpoints vulnerable to the latest threat as well as automatically remediating the issue.
Don't get caught on your heels when the next threat strikes. And it will strike. Connect with one of our experts today to learn more about Endpoint Health.
To get further guidance read The Cybersecurity and Infrastructure Security Agency's Apache Log4J Vulnerability Guidance here.
About Adaptiva
Adaptiva’s Endpoint Health automates discovery and remediation of endpoint configuration issues to maintain unprecedented rates of compliance and end-user uptime and satisfaction across your network. Leveraging the Adaptiva Edge platform IT can continuously deliver software, configurations, and patches to endpoints no matter their location whether on the corporate LAN, VPN, or over the public internet. The world’s largest enterprise organizations and government agencies rely on Adaptiva for best-in-class real-time endpoint visibility and content delivery, as well as automated compliance checks, remediations, and patching without ever throttling the network or the end user experience.