This week’s snacks include:
- 19-Year-Old WinRAR Security Bug Finally Patched!
- IIS Bug Allows DoS Attacks to Force 100% CPU Usage
- Think You Are Safe with Your Password Manager? Think Again.
Happy nibbling!
19-Year-Old WinRAR Security Bug Finally Patched!
Bite
Due to a WinRAR security bug in every version for the last 19 years, IT admins who rarely worried about WinRAR upgrades must now bump up the priority to get this secured.
Snack
Basically, WinRAR has been shipping with a DLL that was compiled in 2006 and—surprise, surprise—it’s not secure. The bug allows remote code execution when extracting files in the ACE compression format. Sure, ACE is not that common, but that doesn’t matter. If a user extracts a malicious ACE file, even one renamed as a RAR file, they’ve executed malware.
RARLab has decided to solve the problem by removing support for the ACE file format.
WinRAR does not have an autoupdate feature, so IT admins need to proactively apply version 5.70 using a software deployment tool such as ConfigMgr.
Meal
Get all the details in this SearchSecurity article titled,WinRAR bug found and patched after 19 years.
IIS Bug Allows DoS Attacks to Force 100% CPU Usage
Bite
Microsoft Security Response Center publishes security fix after denial of service (DoS) issue causes 100% CPU spike in IIS.
SnackGal Goldshtein, a software engineer with F5 Networks, discovered a vulnerability with IIS, whereby the HTTP/2 spec allowed a client “to specify any number of SETTINGS frames with any number of SETTINGS parameters.” Excessively configuring the settings sent IIS into chaos, as it attempted to process the request, sending CPU usage crazy until a timeout occurred and the connection closed.
The HTTP/2 protocol is the next major release version of HTTP aimed at improving performance, amongst other improvements.
To address the issue, Microsoft issued a bunch of security fixes, along with a KB to recommend the HTTP/2 Settings thresholds, after initially stating “Thresholds must be defined by the IIS administrator, they are not preset by Microsoft.”
Use your ConfigMgr to apply the following updates:
- Windows 10 Version 1607 & Windows Server 2016 – KB4487006
- Windows 10 Version 1703 – KB4487011
- Windows 10 Version 1709 & Windows Server, version 1709 – KB4487021
- Windows 10 Version 1803 & Windows Server, version 1803 – KB4487029
The article Define thresholds on the number of HTTP/2 Settings parameters exchanged over a connection gives details on the threshold settings to be applied.
Meal
Read about the vulnerability in the ZDNet article, Microsoft publishes security alert on IIS bug that causes 100% CPU usage spikes and check out the Microsoft Security Advisory with links to all the KB’s to apply in your environment.
Think You Are Safe with Your Password Manager? Think Again.
Bite
New research shows that leading password managers are not as impenetrable as they’d like to you think, but they’re still better than the alternatives.
Snack
We know the old ways of tracking passwords are insecure: from Post-it notes to a “God” password on all accounts to saving passwords in Notepad on the desktop. The rise of password managers solves this … or so we thought.
A recent study, Password Managers: Under the Hood of Secrets Management, found that password managers revealed fundamental flaws and that trivial secret extraction was possible from a locked password manager. This included the ability to unlock the master password, in some cases.
Password managers themselves are a target for hacking, due to the mass collection of the data they store. Vulnerabilities in the products are therefore of a major concern to anyone using them.
Researchers had previously identified flaws in the password managers. Therefore they expected to find improvements in the most recent study. However they still discovered the ability to read the master password from the computer’s memory in plain text format.
The advisory was keen to conclude that, whilst flaws exist, password managers are a good thing and should be utilized for improved security management.
Vendors were quick to refute the claims in the study, however, stating that these were theoretical scenarios. In the real world they either effected legacy applications running on a small percentage of devices or that the realistic threat from the issue was extremely limited.
Any IT Pro should be using password managers wisely and the NCSC in the UK offers some thoughts and guidelines on their usage.
A poll this week from ThreatPost had some interesting conclusions a well. Though this was a “snap poll,” their readership is security-focused and the results heavily favor using password managers.
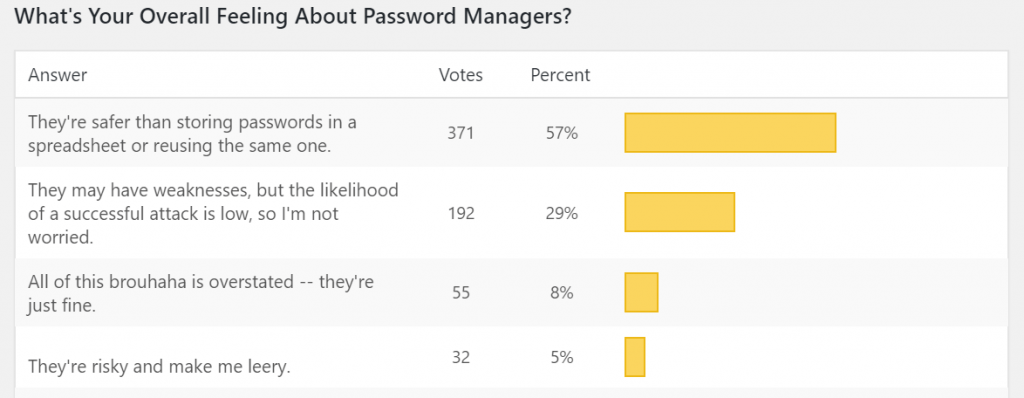
Meal
Read the details of the study at Password Managers: Under the Hood of Secrets Management. You may also want to read the . vendors’ rebuttal, Password Manager Firms Blast Back at ‘Leaky Password’ Revelations.






