IT pros worldwide agree that Microsoft Windows 10 is a security must-have for enterprises. In an Enterprise Endpoint Security Survey, respondents ranked security capabilities highest amongst features compelling them to move to Windows 10.
Many people, however, are unsure exactly what features and capabilities Windows 10 offers. To that end, with help from my colleagues Ami Casto and Chaz Spahn, I have created this Windows 10 Security Primer Infographic.
The infographic organizes security features and capabilities by operating phase (offline, boot, logon, running).
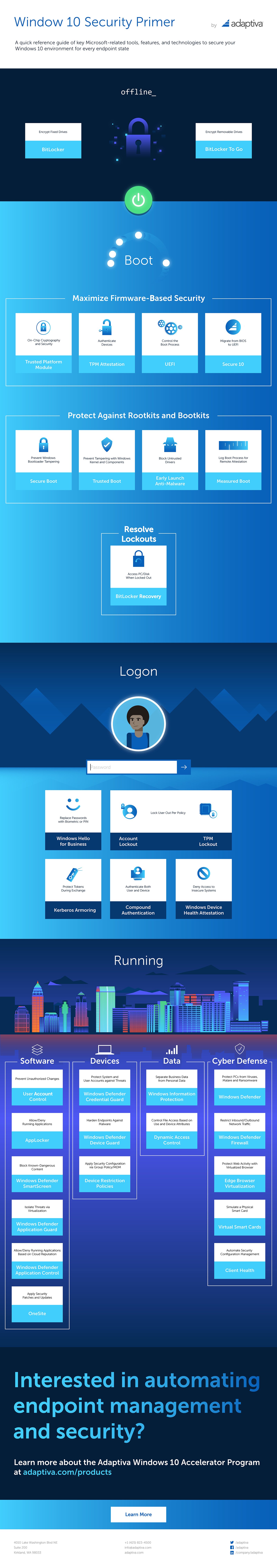
Offline
Encrypt Fixed Drives
BitLocker is robust encryption technology from Microsoft that can encrypt an entire disk, including boot disks. Learn more.
Encrypt Removable Drives
BitLocker to Go secures removable media such as USB drives. Learn more.
Boot
Maximize Firmware-based Security
Windows 10 includes capabilities that help enterprises secure systems by leveraging capabilities now available in endpoint firmware.
On-Chip Cryptography and Security
Windows 10 can use a Trusted Platform Module (TPM) to enhance security. A TPM is hardware-based security consisting of a separate processing module with shielded memory. It can authenticate a unique physical device, and generate and store encryption keys. It can also take and store security measurements. Learn more.
Authenticate Devices
TPM Attestation verifies that a device has an operational TPM chip, and further verifies that the TPM is trusted. Once a device is known to have a valid TPM, the authenticity of the device can be validated (this actually is Kelly Mason’s laptop and not an imposter). Learn more.
Migrate from BIOS to UEFI
Secure 10 is a solution provided by Adaptiva to automate and speed the process of migrating large numbers of endpoints from using legacy BIOS to booting with UEFI. The solution includes a set of documentation and Microsoft System Center Configuration Manager task sequences. Contact us to learn more.
Control the Boot Process
Windows 10 leverages UEFI, advanced firmware that provides a number of hardware-based security capabilities that are available throughout the boot process. Learn more.
Protect Against Rootkits and Bootkits
Windows 10 includes a series of features to prevent malicious code from infecting an operating system at the lowest levels including the boot loader, the OS kernel, and boot drivers.
Prevent Windows Bootloader Tampering
Secure Boot ensures that boot software has a valid signature. This prevents tampering with software that loads the Windows 10 kernel. Learn more.
Prevent Tampering with Windows Kernel and Components
Trusted Boot verifies that the Windows 10 kernel itself has not been tampered with. Learn more.
Early Launch Anti-Malware (ELAM)
ELAM prevents malware from infecting a system at the boot driver level by allow only trusted drivers to load during Windows 10 boot. Learn more.
Measured Boot
Measured Boot will log all boot activities to a server, where they can be analyzed for signs of infection or tampering. Learn more.
Resolve Encryption Lockouts
Access PC/Disk When Locked Out
BitLocker Recovery allows access to a hard disk when the user is locked out. A recovery key may be generated in different ways, depending on how BitLocker was set up. Learn more.
Logon
Replace Passwords with Biometric or PIN
Windows Hello for Business replaces traditional password with biometrics—thumbprint readers, facial recognition, etc.—and PINs. Learn more.
Lock User Per Policy
Windows 10 can automatically lock users out when security is in question. This can be as simple as locking out an account after a set number of failed password entries, or more complex. Learn more.
In addition to account lockout, Windows 10 can increment a TPM counter (an on-chip counter that can be incremented once each time a suspicious activity occurs). A TPM lockout occurs when the counter on a TPM chip exceeds a threshold. While in effect, the TMP will refuse authorizations by returning an error in response to command requests. Learn more.
Protect Tokens During Exchange
Kerberos Armoring secures communication between a domain-joined client and its domain controller to prevent spoofing that could allow password-based attacks. Learn more.
Authenticate Both User and Device
Compound Authentication ensures that the unique combination of user and device is authenticated, not just user or device. Learn more.
Deny Access to Insecure Systems
Windows Device Health Attestation allows administrators to allow or deny access to corporate resources based on device health. Systems are checked and run time, and can only access corporate resources if correctly running key security components (e.g., ELAM, BitLocker, Secure Boot, and code integrity). Learn more.
Running
Software
Prevent Unauthorized Changes
User Account Control (UAC) ensures that only administrators can install applications. Learn more.
Allow/Deny Running Applications
AppLocker whitelists applications so only approved applications can run on an endpoint. Learn more.
Block Known-Dangerous Content
Windows Defender SmartScreen connects to a service to make sure that software you have downloaded and are about to run is not malicious. It does this by checking it against a database of known-good software. Learn more.
Isolate Threats via Virtualization
Windows Defender Application Guard can protect your system by isolating applications in their own virtualized environment. Learn more.
Allow/Deny Running Applications Based on Cloud Reputation
Windows Defender Application Control intelligently restricts which applications, scripts, plug-ins, etc., can run on a system. Learn more.
Apply Security Patches and Updates
Adaptiva OneSite Anywhere, working with Configuration Manager, protects endpoints by keeping software up to date. OneSite rapidly deploys and applies patches at scale using a secure peer-to-peer model. Learn more.
Devices
Protect System and User Accounts Against Threats
Windows Defender Credential Guard protects password using virtualization-assisted security. Learn more.
Harden Endpoints Against Malware
Windows Defender Device Guard prevents malware from running on a system using a variety of techniques. Learn more.
Apply Security Configuration via Group Policy/MDM
Microsoft empowers systems administrators to apply device restrictions policies via group policy or MDM. For enterprises using group policies, a Security Compliance Toolkit is available to help test and customize Microsoft-recommended configurations. Learn more.
Data
Separate Business Data from Personal Data
Windows Information Protection allows enterprises to separate corporate and personal data and set restrictions for each. For example, a user may not be able to share, copy, or print corporate data while given free reign with their cat pictures. Learn more.
Control File Access Based on User and Device Attributes
Dynamic Access Control is the ability to change permissions on the file system on different systems through the enterprise on the fly in real time. Learn more.
Cyber Defense
Protect PCs from Viruses, Malware and Ransomware
Windows Defender protects PCs from viruses, malware, and ransomware. Windows Defender has been improved in Windows 10 to the point where many security experts suggest using it over traditional third-party antivirus solutions. Learn more.
Restrict Inbound/Outbound Network Traffic
Windows Defender Firewall with Advanced Security provides two-way traffic filtering for a device. The software is intelligent, meaning it will do basic configuration automatically. It works with other Microsoft network security technologies, managed through the Windows Defender Firewall interface. Learn more.
Protect Web Activity with Browser Virtualization
Microsoft Edge runs each instance of the browser in its own virtual machine to limit the damage attackers can do. Internet-acquired malicious software cannot access the Windows 10 operating system or file system, just what is exposed to Edge’s virtual machine. Learn more.
Simulate a Physical Smart Card
In a two-factor authentication scenario that would normally require a physical smart card, a virtual smart card can be used instead. This Windows 10 technology requires use of a system’s TPM chip. Learn more.
Automate Security Configuration Management
Adaptiva Endpoint Health allow automation of security configuration management, including identification and remediation in the event of deviations from corporate policy.
Summary
While keeping your company safe in today’s environment is challenging, it’s also possible. Windows 10 is revolutionizing endpoint security in enterprises. It offers capabilities that help administrators stay ahead of cyberattackers in every phrase of operation.
Mastering Windows 10 security is a huge step in your security success as you deploy and use the OS. I wish you the best as you fight the dark side!






