Reaching Your Clients
As the workforce becomes increasingly mobile, IT pros are finding it harder to manage endpoints. This is especially true if you work at a large company using Microsoft System Center Configuration Manager (ConfigMgr). You may have a roaming sales force, home office users, and/or Internet-connection-only offices. These systems may rarely phone home to the mothership (ConfigMgr). Hitting your monthly target for software update compliance (also known as patch compliance) can be a challenge for these devices.
With your ConfigMgr implementation, you need a way for Internet-connected clients to retrieve policy and content. Traditionally if you wanted a client connected by the Internet to receive policy and content, you needed to implement an Internet-Based Client Management (IBCM) infrastructure. This involved installing a one or more site servers in your DMZ with a Management Point (MP), Distribution Point (DP), and Software Update Point (SUP) roles. Then you poke all the necessary holes in your network to allow communication between the DMZ servers and your ConfigMgr site server inside the corporate network. Are you exhausted just reading about it? It can be just as painful getting the buy in from the networking and security teams and implementing it.
Microsoft introduced the Cloud Management Gateway (CMG) as a simpler, more secure, and cost-effective approach to reaching clients on the Internet. They introduced it as a pre-release feature in 1610 and promoted it to a released feature in 1802. It allows you to extend your reach to Internet-facing clients without setting up additional site servers and roles and poking holes in your network perimeter. The gateway is a provisioned Azure cloud service, essentially a canned virtual machine. It is published with an Internet-facing IP address, allowing clients to authenticate with either certificates through the classic service deployment or with Azure AD through Azure Resource Manager deployment.
The gateway acts as a middle-man allowing clients to communicate with the Management Point and Software Update, enabling it to obtain policy and perform WSUS scans. Your clients obtain content directly from a Cloud Distribution Point (CDP), or alternatively directly from Microsoft Update for software update content.
How Much Does It Cost?
When deploying a CMG you will pay a base monthly cost for the number of instances that you create, and then a variable cost for data storage and data transfer.
Azure Pricing
To estimate your monthly cost you will want to leverage the calculators at Azure pricing and Azure pricing bandwidth. The below sample estimates are based on a single CDP/CMG for the US East region for 2,000 devices mid-year 2018.
- Base monthly cost of a CMG (A2 Standard VM) would be $99.28/month
- Variable monthly cost for data transfer 100MB/month per device X 2000 devices (195GB) would be $16.55/month.
The CDP pricing will vary greatly depending on what content you are making available, and how often clients will be downloading the content. The rate is typically $0.087 per GB/month up to 10 TB a month. For example, if you have 100 devices perform a one-time download of a 7GB package that would cost approximately $60.46. You can set thresholds to alert you if you are close to exceeding predefined limits.
Getting Started
This blog will focus on the classic service deployment which is necessary unless your clients are Azure AD joined, then you may use the Azure Resource Manager deployment for authentication. In using the classic service, you will need to implement the following:
- Configure a service connection point
- Create certificates for client/server authentication and Azure management
- Deploy the Cloud Management Gateway
- Configure site roles (MP and SUP)
- Deploy Cloud Distribution Point (as needed)
The requirements are:
- Azure subscription and someone with Azure administrator permissions
- CMG connection point
- Service connection point in online mode
- Server authentication certificate
- Azure management certificate (for classic mode)
Service Connection Point
If you are using Current Branch, you likely already have a service connect point configured. This role is required to check the Configuration Manager cloud services for updates. It is a pre-requisite for the cloud management gateway. To add this role:
- Navigate to Administration\Overview\Site Configuration\Servers and Site System Roles
- Right click on the desired site server, and choose Add Site System Role
- On the Specify roles for this server, chose the Service Connection Point
- For the connection type, choose online, persisted connection and completed the wizard
Online, persisted connection is a requirement for the CMG as it requires and online connection. Offline mode allows you to use the Service Connection Tool to download and sneaker net updates to your ConfigMgr site server. However, if you have your site in an isolated environment without internet access then you will not be able to use the CMG.
Certificates
Microsoft published detailed instructions so we won’t rehash all the details, but we will give you a clear summary of what you need and why you need it. While it is possible to use self-sign certificates, we strongly recommend to only use them for a lab environment and to use PKI for production for security reasons. You will need the following certificates:
Server Authentication
This CMG server authentication certificate must be issued by a certificate authority trusted by your clients. It can be from a publicly trusted provider such as VeriSign, or from your internal certificate authority from PKI. We recommend the PKI route, which avoids the need to setup a CNAME record in your public DNS. When generating the PKI certificate, you use the same template you would for a cloud distribution point, except for the common name you specify the servicename.cloudapp.net. The cloudapp.net is the domain owned by Microsoft and they publish the external DNS for this service address when you create your CMG. You will want to check for the availability for the desired service prior to creating your CMG, something like contosocmg.cloudapp.net.
Azure Management
This certificate is required for classic mode, and the certificate must be uploaded to the Azure subscription service by your Azure administrator prior to creating your CMG. While your Azure administrator is hanging out on the Azure Portal, they will want to copy the Subscription Service ID. Going the PKI route, you can export the same certificate used for the server authentication, as a CER file without a private key, and upload to the subscription. You will use an export of the same certificate with as PFX file with the private key when creating the CMG.
Client Authentication
A client authentication certificate that chains to a trusted root certificate. Typically, this would be a certificate that your devices auto-enroll in based on a group policy.
Deploy the Cloud Management Gateway
- Navigate to Administration\Overview\Cloud Services in the console.
- Right click on Cloud Management Gateway and choose Create Cloud Management Gateway.
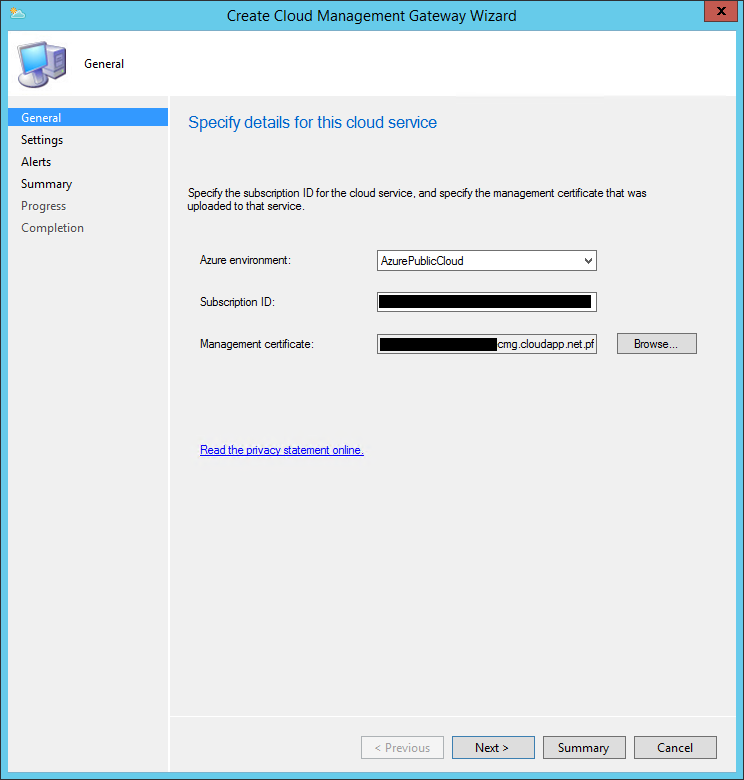
- Choose your Azure environment (likely AzurePublicCloud), paste the Subscription ID provided by your Azure Administrator.
- Browse to the private certificate you exported for your CMG, enter the password when prompted (you should have created this password when you exported the certificate) and click Next.
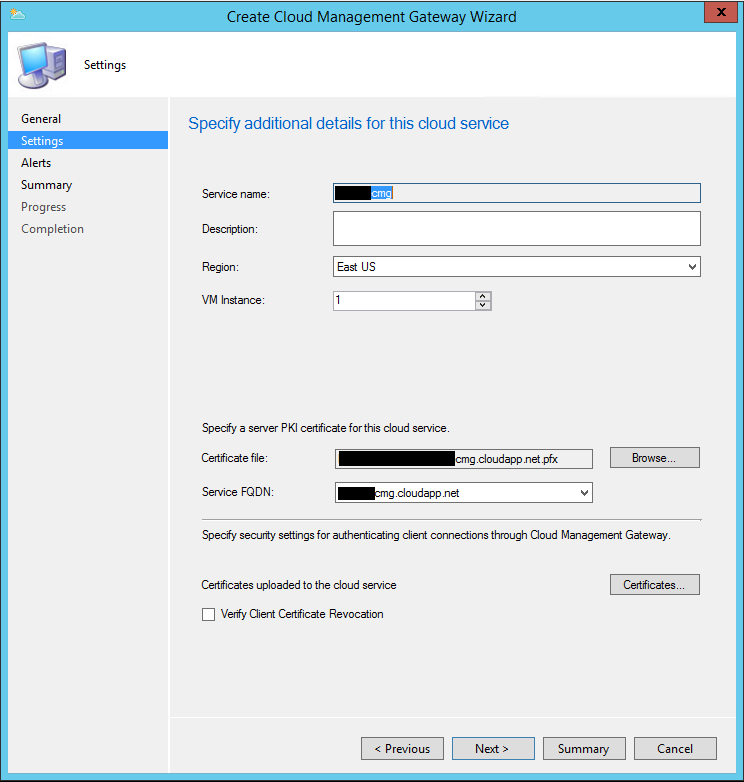
- Choose the Region you want to host your CMG, it should be closest to your clients. You can create multiple Gateways if you need coverage in each region, and you can create multiple VM instances if you need to provide redundancy or scale. We recommend that you start with one as you perform your proof of concept, so you can get a good feel for the cost prior to scaling out your infrastructure.
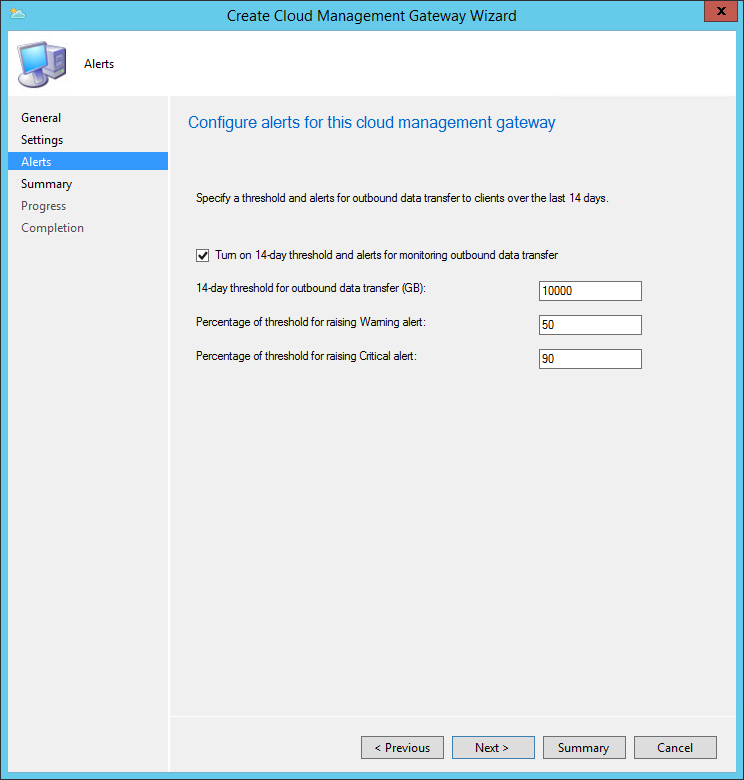
- You can define threshold alerts, this is a means to make sure you do not inadvertently exceed the desired cost. You will want to ensure that you have connected the ConfigMgr alerts to an email or monitoring solution to ensure you are notified of these alerts, otherwise you will need to check the console regularly for alerts.
- Finally, you are provided the standard summary screen, chose Next to begin provisioning you CMG.
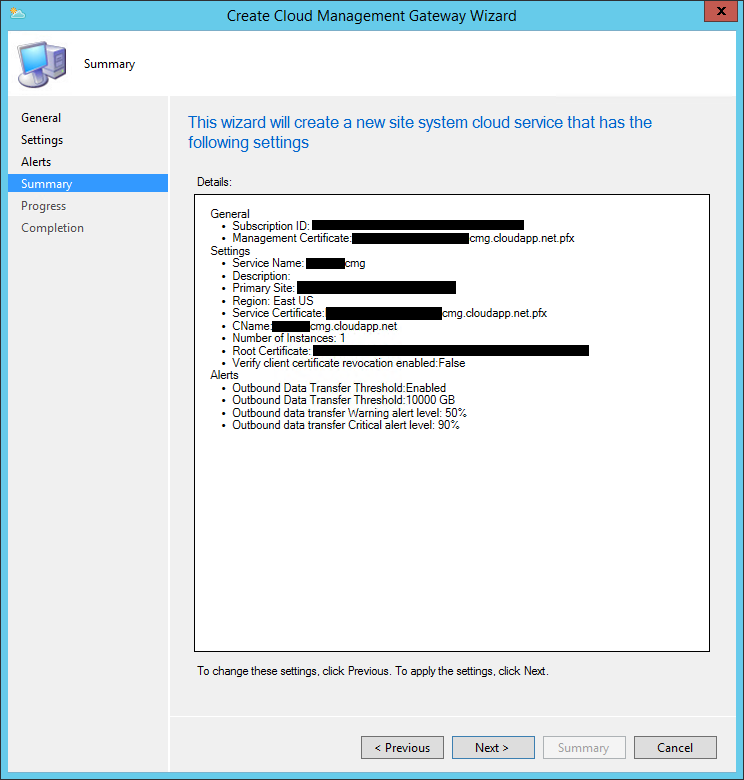
Navigate back to the Cloud Management Gateway node in your console and you can monitor the progress: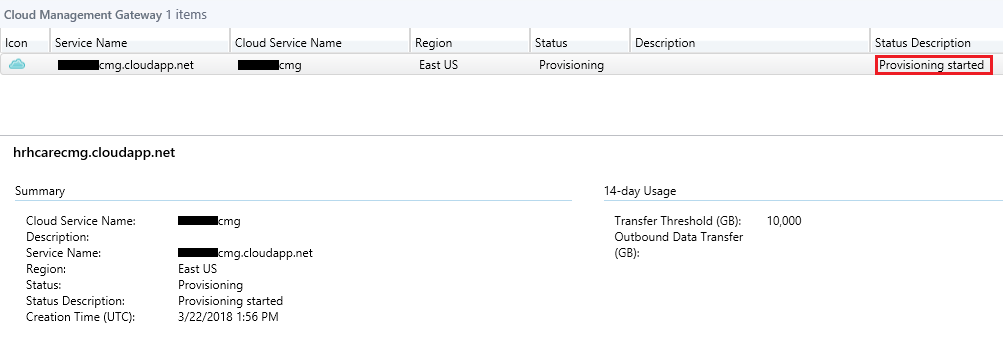
Configure Site Roles
Now that you have provisioned your CMG and configured the proxy service, you need to enable the MP/SUP roles to enable clients to communication with your infrastructure. It requires these roles to configured for HTTPS communication role. If you currently use HTTP mode for your intranet clients (on premise) then you will need to add a new MP/SUP role that can be enabled for HTTPS for the CMG.
Management Point
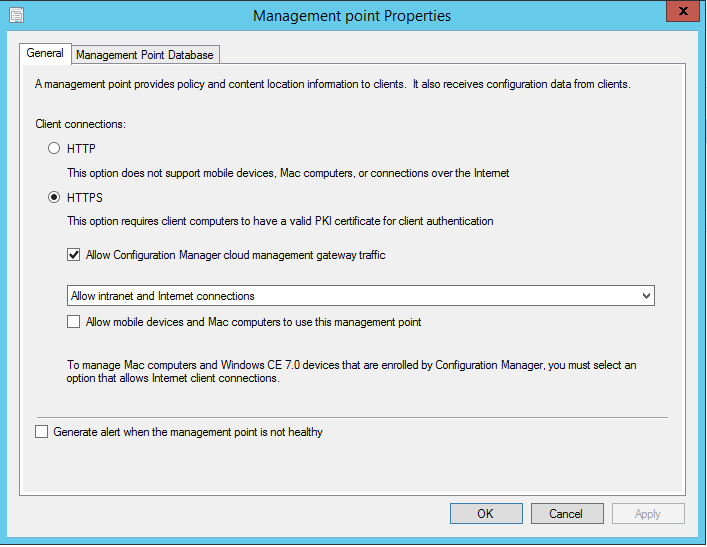
To enable the management point for use by the CMG:
- Navigate to \Administration\Overview\Site Configuration\Servers and Site System Roles.
- Click on the Site Server with the MP you are enabling, and double-click on Management point to open the properties.
- Select HTTPS mode, click the Allow Configuration manage cloud management gateway traffic checkbox, and ensure Allow intranet and internet client connections is selected.
Software Update Point
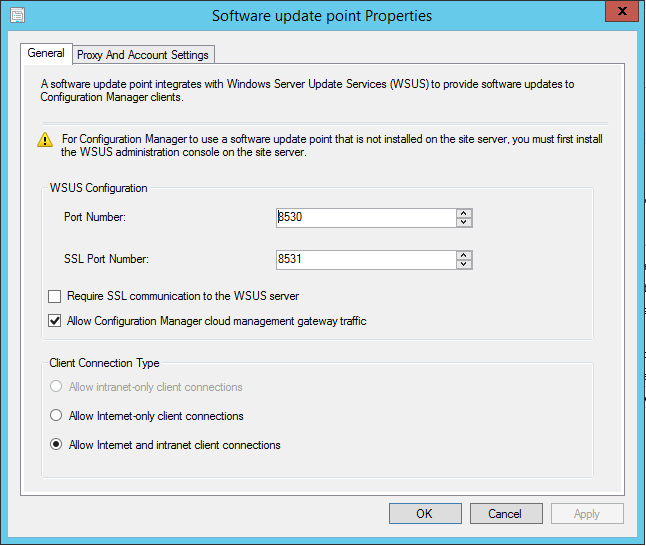
If you plan on allowing clients to scan for software updates, you need to enable your SUP for use by the CMG:
- Navigate to \Administration\Overview\Site Configuration\Servers and Site System Roles.
- Click on the Site Server with the MP you are enabling, and double-click on Software update point to open the properties.
- Select Allow Configuration manage cloud management gateway traffic checkbox.
Deploy the Cloud Distribution Point
While it is not a requirement to deploy a Cloud DP when using a CMG, it is necessary if you want to make content available to clients on the Internet.
Content for Software Updates only
If you are only concerned with software updates, you can be sure to just enable access to Microsoft Update on your software deployments as follows: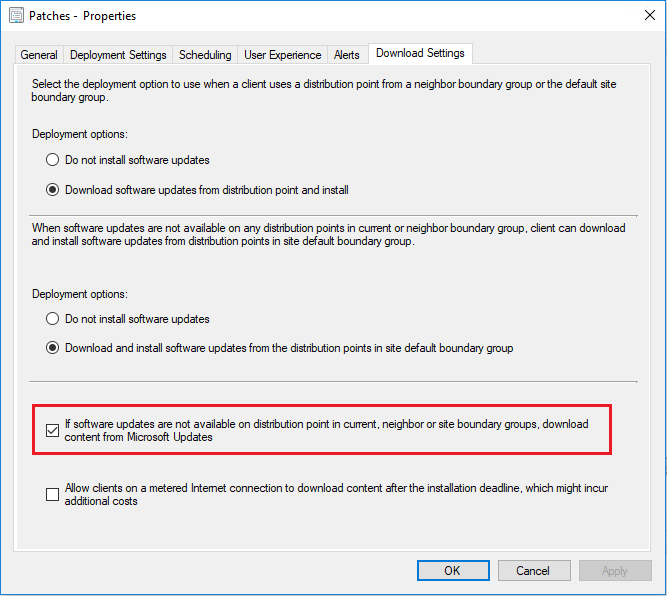
Cloud Distribution Point
If you do not want clients downloading updates directly from Microsoft Update, you can setup a Cloud Distribution Point as follows:
- Navigate to Administration\Overview\Cloud Services in the console.
- Right click on Cloud Distribution Points and choose Create Cloud Distribution Point.
- Choose your Azure environment (likely AzurePublicCloud), enter your Subscription ID, Browse and add your Private Certificate.
- Choose your region, and import your Cloud DP certificate.
- Choose your alerts for data storage and data transfer.
- Review the settings on the summary and choose Next to provision your Cloud DP.
What may be confusing compared to setting up the CMG, is that you need to use your public domain name when creating a certificate for the Cloud DP. You will not use something like sccmdp.cloudapp.net, but rather something like sccmdp.contoso.com. In addition, you will need to create your own public-facing DNS record for this so that clients are able to resolve the name and connect to it from the Internet.
As of the 1802 ConfigMgr public release, this was your only option to make content available to internet facing clients in conjunction with your CMG. However, Microsoft has continued its investment in the CMG. In the 1806 public release, the CMG can be used without the additional setup and cost of a Cloud Distribution Point. This allows the gateway to act as a middleman for a distribution point as well, eliminating the need to pay a monthly fee for a CDP virtual machine, and storage costs. You will stay pay for the data transfer usage.
Logging
True to the nature of ConfigMgr, there are multiple log files for digging behind the scenes to monitor the service or troubleshoot issues.
Server Logs
On the site server hosting the various roles, you can look at the following log files:
- ClougMgr.log – Log file for the Cloud management gateway connection point.
- SMS_Clolud_ProxyConnector – Log file for the connectivity from clients to the proxy services.
For each CMG service and instance, you will find the following log files on the site server:
- CMG-ServiceName-ProxyService_IN_0-CMGSetup.log – Installation and configuration.
- CMG-ServiceName-ProxyService_IN_0-CMGService.log – Installation and configuration.
- CMG-ServiceName-ProxyService_IN_0-CMGHttpHandler.log – Installation and configuration.
Client Logs
On the client there are not logs special to the CMG but you can find information in the standard client log:
- LocationServices.log – You will see here if the client is connecting to the CMG. It needs to receive policy at least once while connected to the corporate network.
- CcmLocation.log – Confirm the client MP is pointing to the CMG.
- CcmMessaging.log – Confirm the client is successfully communicating.
- InternetProxy.log – Activity for both the CDP and CMG.
References
- What is new in ConfigMgr 1806 – https://docs.microsoft.com/en-us/sccm/core/plan-design/changes/whats-new-in-version-1806
-
Service connection point – https://docs.microsoft.com/en-us/sccm/core/servers/deploy/configure/about-the-service-connection-point
-
Internet based client management – https://docs.microsoft.com/en-us/sccm/core/clients/manage/plan-internet-based-client-management
-
Cloud based distribution point – https://docs.microsoft.com/en-us/sccm/core/plan-design/hierarchy/use-a-cloud-based-distribution-point
-
Plan a cloud management gateway – https://docs.microsoft.com/en-us/sccm/core/clients/manage/cmg/plan-cloud-management-gateway
-
Certificates for the cloud management gateway – https://docs.microsoft.com/en-us/sccm/core/clients/manage/cmg/certificates-for-cloud-management-gateway






