IT Pros already know why they care about using best practices to strengthen endpoint security. What they really want to know is how.
That’s a question the nonprofit Center for Internet Security® and their 20 CIS Controls™ help to answer. An international community of IT experts created the controls, sets of recommended security actions to take. The controls define a defense-in-depth set of best practices designed to protect systems and networks against the most common attacks.
The CIS Controls are based on five tenets:
Offense informs defense. Real-world data of what attacks are actually happening should be used to inform defense.
Prioritization. Put current efforts into providing the greatest protection based on your means and environment.
Measurements and metrics. Using the same measuring stick across systems and organizations so that results can be meaningfully studied and the results used to improve defenses.
Continuous diagnostics and mitigation. Let the effectiveness of existing security activities determine priorities for improving defenses.
Automation. Greater automation gives an organization greater ability to execute and improve on the first four tenets.
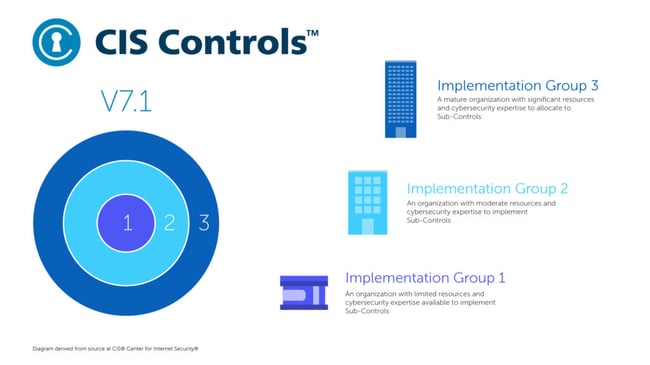
The current release is Version 7.1, which introduced the concept of Implementation Groups (IG’s). The IG’s help organizations prioritize implementation. IG1 should be applied first, then IG2, and then IG3.
- IG1: Basic controls that should be applied first in all organizations.
- IG2: Foundational controls that should be applied in medium and large organizations. Small businesses may consider implementation if they have time/resources.
- IG3: Organizational controls that will generally apply only to larger organizations.
CIS Controls V7.1 Implementation Groups
Though the framework provides 20 controls, this blog series will address only the first five. These are important endpoint management controls that apply to every organization.
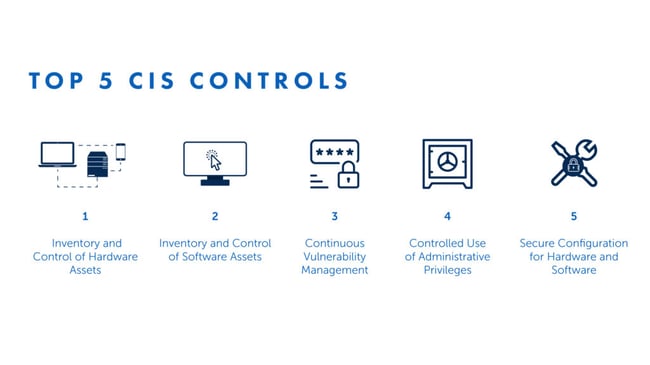
CIS Control 1: Inventory and Control of Hardware Assets
CIS Control 2: Inventory and Control of Software Assets
CIS Control 3: Continuous Vulnerability Management
CIS Control 4: Controlled Use of Administrative Privileges
CIS Control 5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers
Each control defines a group of sub-controls, specific actions you can take. To help you understand the high-level purpose of each sub-control, the CIS assigns each one an attribute of identify, respond, or protect.
In this series opening blog, I’ll cover CS1. I’ll cover CS2 through CS5 in four subsequent blogs.
CIS Control 1: Inventory and Control of Hardware Assets
The official CIS definition is:
Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.
To secure your devices you have to know what devices to secure.
The struggle is real. Many organizations have systems they don’t know they have. Well, somebody probably knows, but not the people in charge of endpoint security (or their management systems). Obviously if a system is not known, it can’t be brought into compliance with security policy, scanned for malware, or quarantined in the event of a cyberattack.
CIS Sub-Control 1.1 (Identify): Utilize an Active Discovery Tool
The official CIS definition is:
Use an active discovery tool to identify devices connected to the organization’s network and update the hardware asset inventory.
An active discovery tool will sweep for unknown devices on the network, such as those not registered in a directory or database. Endpoint management tools (e.g., Microsoft Endpoint Manager) can do this to some extent. IT pros can also choose from a variety of available tools and techniques to actively scan. The scans should be done regularly.
CIS Sub-Control 1.2 (Identify): Use a Passive Discovery Tool
The official CIS definition is:
Utilize a passive discovery tool to identify devices connected to the organization’s network and automatically update the organization’s hardware asset inventory.
Passive discovery tools watch network traffic for activity from systems not tracked in the hardware asset inventory. They can be placed around the network. When unregistered devices are found, they must be added to the inventory either manually or thought an automated process.
CIS Sub-Control 1.3 (Identify): Use DHCP Logging to Update Asset Inventory
The official CIS definition is:
Use Dynamic Host Configuration Protocol (DHCP) logging on all DHCP servers or IP address management tools to update the organization’s hardware asset inventory
Every device connecting to the network will have an IP address, commonly provided by a DHCP server. A log of address assignments can be used to help identify unauthorized systems.
CIS Sub-Control 1.4 (Identify): Maintain Detailed Asset Inventory
The official CIS definition is:
Maintain an accurate and up-to-date inventory of all technology assets with the potential to store or process information. This inventory shall include all assets, whether connected to the organization’s network or not.
Document your organization’s technology assets in a database, and keep that database current. The inventory should include both networked and non-networked devices.
CIS Sub-Control 1.5 (Identify): Maintain Asset Inventory Information
The official CIS definition is:
To secure your devices you have to know what devices to secure. Ensure that the hardware asset inventory records the network address, hardware address, machine name, data asset owner, and department for each asset and whether the hardware asset has been approved to connect to the network.
Once you’ve implemented an asset inventory per sub-control 1.4, you can make it better. This sub-control enumerates specification information that you should be including:
- network address
- hardware address
- machine name
- data asset owner
- department for each asset
- whether the hardware asset has been approved to connect to the network.
CIS Sub-Control 1.6 (Respond): Address Unauthorized Assets
The official CIS definition is:
Ensure that unauthorized assets are either removed from the network, quarantined or the inventory is updated in a timely manner.
The only responsive sub-control, it suggests that you don’t allow unauthorized assets to operate once you know about them. You can pull them off the network, quarantine them, or authorize them (update the inventory). Just don’t do nothing. You need to, act and pretty quickly.
CIS Sub-Control 1.7 (Protect): Deploy Port Level Access Control
The official CIS definition is:
Utilize port level access control, following 802.1x standards, to control which devices can authenticate to the network. The authentication system shall be tied into the hardware asset inventory data to ensure only authorized devices can connect to the network.
Once you have taken action to comply with sub-controls 1.1 through 1.6, you can lock things down. Don’t allow any unauthorized devices to authenticate to the network. In practical terms, this means that you use 802.1x standards to only allow devices authorized in the inventory database to authenticate.
CIS Sub-Control 1.8 (Protect): Utilize Client Certificates to Authenticate Hardware Assets
The official CIS definition is:
Use client certificates to authenticate hardware assets connecting to the organization’s trusted network.
By using client certificates you can add an additional level of protection. A key will be assigned to authorized systems, and the key must be valid for the system to interact with network services. Administrators can easily revoke a client’s certificate. If implemented, this can also help when quarantining unauthorized devices.
Learn More
If you are an endpoint management IT pro, you need to understand the CIS Controls. Even if you do not implement them in your environment, an awareness may help you make smarter security decisions. If you’d like to learn more about the CIS Controls, you can download a new report from Adapitva, Top 5 CIS Controls and Cybersecurity Best Practices Report.






