Challenges to Improving Endpoint Compliance
Our newest research with Ponemon Institute titled, “Managing Risks and Costs at the Edge” paints a stark picture of the IT landscape; one that has devolved into a reactionary state of catch up. Current technologies no longer enable IT professionals to stay ahead of threats, maintain compliance, or have visibility into all the devices across their organizations. These issues are mission critical and IT teams need modern tools to be successful. Complicating matters, IT budgets and headcounts are expanding but the money is typically being used to fix the same old problems while making roles and responsibilities unclear. IT departments need a new paradigm, not inflated budgets. Four key areas keep IT professionals up at night. Let’s look at each to understand why they are so important and what organizations should do to address them.
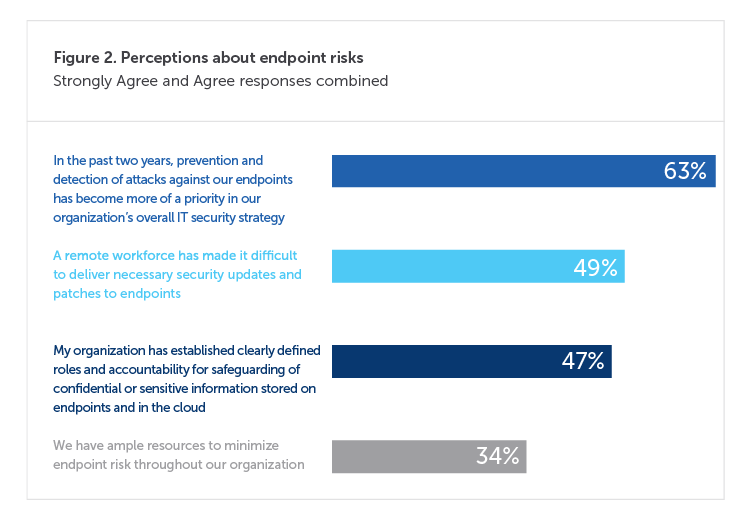
The highest-level threats include ransomware, zero-day attacks, DDoS attacks, credential theft, and distribution point sprawl. Bad actors only need to get lucky once, but IT departments must be hypervigilant all the time. But the playing field is not level. According to our latest research, few organizations allocate enough resources to minimize endpoint risk. Organizations have made prevention and detection more of a priority over the past two years. But only a third say their organizations are set up to properly minimize such threats. This is exacerbated by the dramatic increase in a remote workforce that logs onto the network from anywhere and everywhere.
| Do | Don't |
|---|---|
|
Invest in endpoint management apps that are powered by your devices to get real-time visibility into every endpoint in real-time. Rely on distributed infrastructure to get real-time visibility into every endpoint in real time. |
Waste budget on software that relies on centralized infrastructure and can't scale to track remote endpoints. |
|
Reduce your attack surface by keeping your endpoints up to date and in compliance. |
Leave your endpoints vulnerable. |
|
Reduce agent sprawl with decentralized endpoint management applications. |
Add more endpoint agents that make managing devices more of a hassle. |
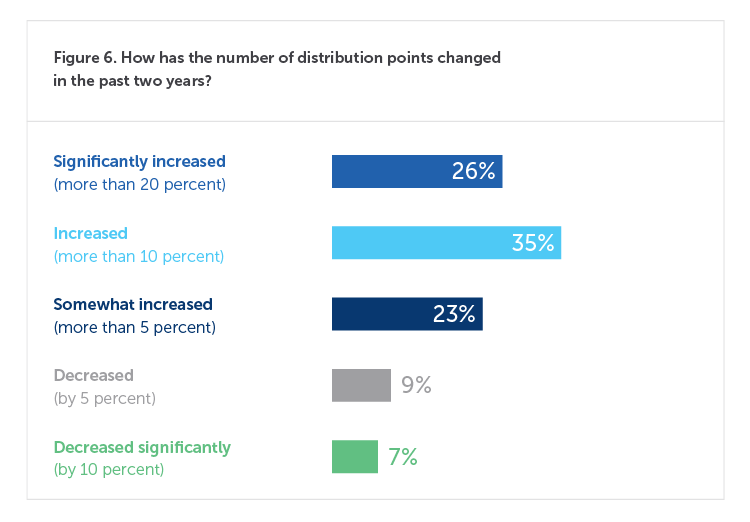
For every six new endpoints, an organization must stand up one new distribution server. Surveyed organizations from our latest research study with Ponemon Institute have an average of 22,925 distribution points, which have increased significantly for 26% of respondents. IT infrastructure expansion is out of control, leading to sprawl as those servers, whether on-prem or in the cloud, aren’t effectively protecting all of an organization’s endpoints. The most challenging aspects of this problem include keeping OS and applications up to date, patching and security updates, and configuration health. But it is impossible to secure devices IT can’t see, and legacy servers do a poor job of tracking devices that log in remotely.
| Do | Don't |
|---|---|
|
Effortlessly scale as your organization adds any number of endpoints (laptops, POS, ATMs, etc.) to your network. |
Fall behind the growth of your business. |
|
Rely on endpoint management software that continuously keeps devices up to date and reduces costs so you can stay ahead of endpoint risk. |
Rely on tools that don't help you get ahead of endpoint risk. |
|
Get total visibility and control of every endpoint on your network regardless of scale. |
Let a single endpoint go unnoticed. |
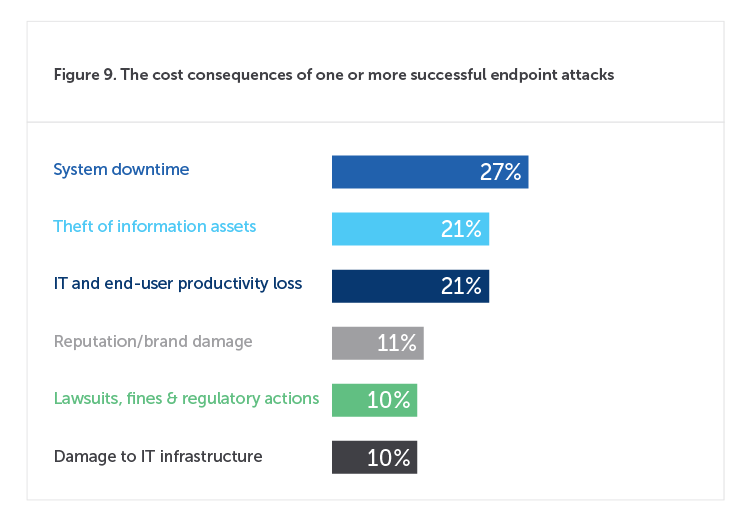
According to research we conducted with Ponemon Institute, on average, employees lose 720 hours of productivity a year due to required software and security compliance updates. And that is just planned downtime. Attacks rob companies of even more productivity to the tune of $1.8 million on average per year not to mention the costs of information loss/theft, brand reputation, and infrastructure corruption. Unfortunately, because distribution point sprawl only sends costs up, organizations are forced to allocate resources to the network at the expense of security.
| Do | Don't |
|---|---|
|
Invest in next generation endpoint management to prevent threats from ever reaching your devices in the first place. |
Waste budget on a patchwork of security solutions that drag you further behind. |
|
Use an incredibly fast peer-to-peer network to deliver patches, updates, and remediations anytime without throttling your network. |
Disrupt employees or wait until off hours to remediate issues or deploy updates and patches. |
|
Save money by remediating endpoint issues before bad actors can find and take advantage of vulnerabilities. |
Let inefficient systems slow down fixes before attacks happen. |
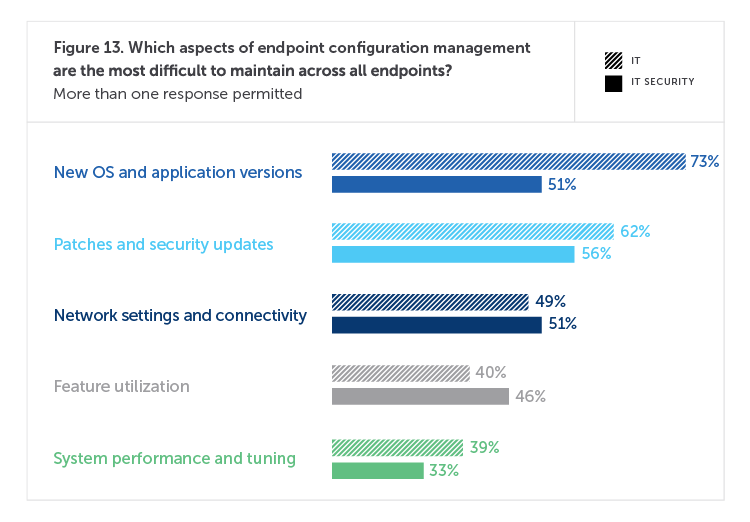
Ideally, IT operations and IT security work in lock step. But survey results indicate otherwise. For example, 73% of IT operations respondents consider new OS and application versions to be the most difficult to maintain across endpoints, compared to 51% of IT security personnel. This would indicate that operations has a better handle on endpoint security than their colleagues. Further evidence of this chasm is seen in the fact that 50% of operations believes their organizations have clearly established roles and accountability while only 43% of security personnel would agree. This is a sizeable difference in understanding the problems they face and who should be responsible.
| Do | Don't |
|---|---|
|
Automate discovery and remediation of configuration issues to keep devices healthy, freeing your IT teams to better integrate. |
Depend on more headcount alone to secure endpoints from increasingly sophisticated attacks. |
|
Use a dashboard that provides visibility into the state of your endpoints to your entire team. |
Manage endpoints in a silo without organizational visibility and transparency. |
|
Provide actionable data, monitoring, and control of endpoints to maintain visibility across compliance and security. |
Disagree on the nature of threats and endpoint compliance. |